kid 3d ago • 33%
That's why I don't use Kaspersky :)
kid 3d ago • 33%
In my opinion, you will always be at the mercy of a government in this context: US, China, Russia. In the end it's a matter of choosing which one. FOSS maybe a little less, but in the end it's almost the same. That's my view, of course. That doesn't mean you can't give them a hard time ;)
kid 3d ago • 91%
This one does not spark joy.
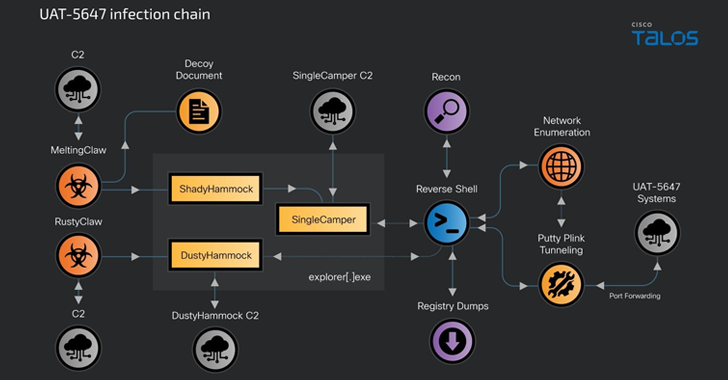
 gbhackers.com
gbhackers.com
 www.helpnetsecurity.com
www.helpnetsecurity.com
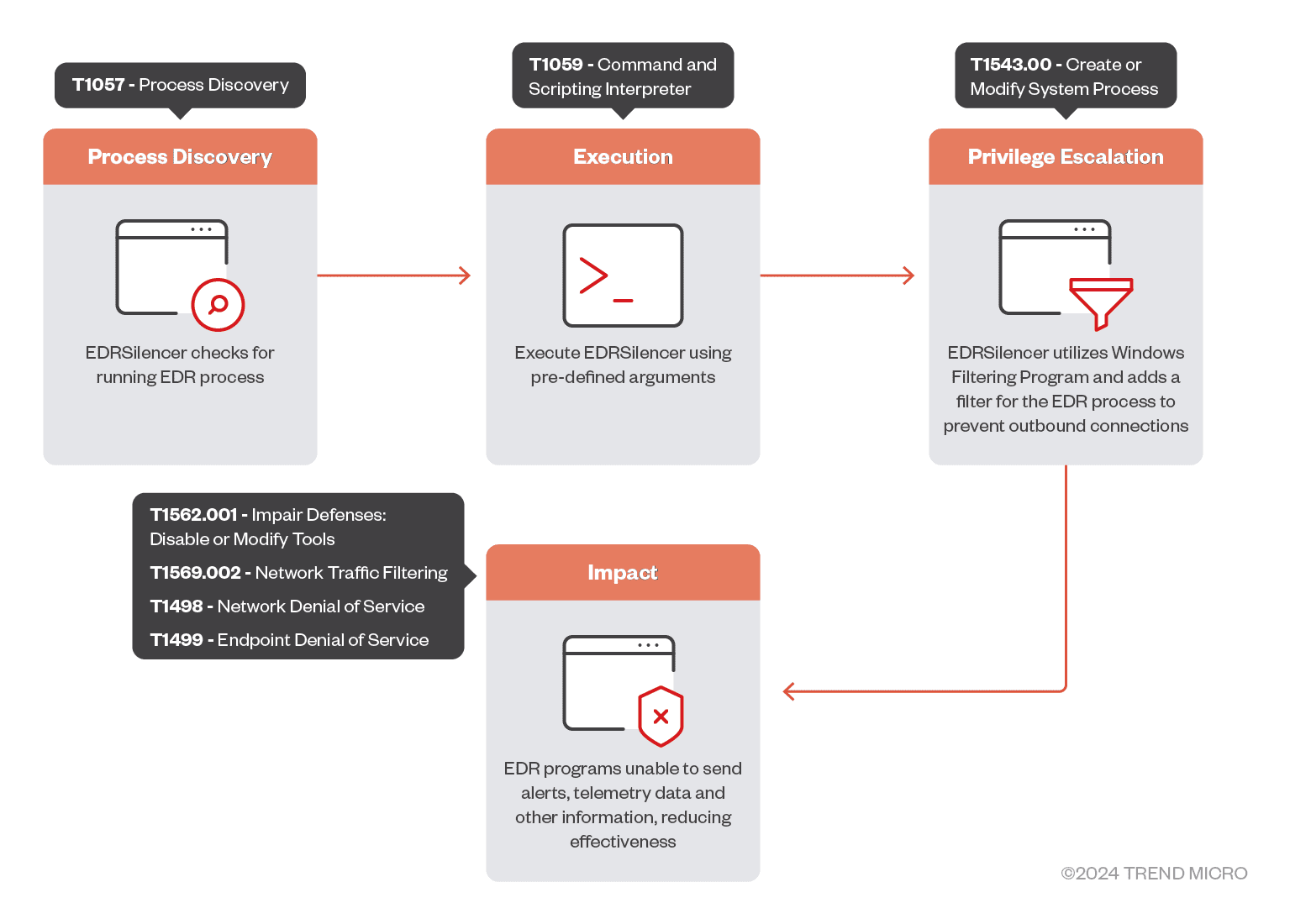 securityonline.info
securityonline.info
EDRSilencer “disrupts the transmission of telemetry or alerts to EDR management consoles,” rendering these security tools ineffective at identifying and removing malware. By leveraging the Windows Filtering Platform (WFP), EDRSilencer blocks network communication from processes associated with various EDR products, creating a blind spot in an organization’s security defenses.
 www.darkreading.com
www.darkreading.com
kid 1mo ago • 100%
Update: Israel Planted Explosives in Pagers Sold to Hezbollah, Officials Say (https://www.nytimes.com/2024/09/17/world/middleeast/israel-hezbollah-pagers-explosives.html)
kid 2mo ago • 100%
You can use https://tails.net/ booting from another flash drive in memory only.
kid 2mo ago • 100%
Take that with a grain of salt.
kid 2mo ago • 100%
Agreed
kid 3mo ago • 100%
I like to use the 2013 Target breach case. They lost $1 billion due to the attack, their stocks dropped significantly after the attack, had several lawsuits, they closed a few stores, and changed the CEO and CIO. But a few months later, all was forgiven, their stocks recovered, and life went on.
Don't get me wrong, the risks of a cyber attack have to be taken seriously. But I feel that I have overestimated the impacts of reputational damage my whole life, as an infosec professional. My thinking was always like this: if you get reputational damage, you are done, no chance to recover, it is the end of it.
I'm following the Crowdstrike case, but I would bet that they will lose some market share (mostly prospects), perhaps some layoffs, but stocks will come up eventually.
kid 3mo ago • 100%
Not as much as if it contained passwords, for sure. Bu it gives a nice mailing list for phishing and so on.
kid 3mo ago • 100%
Depends of the country. Disrupt with Internet/communications may be a crime in some countries.
kid 3mo ago • 100%
Kudos to SOC team.
kid 3mo ago • 100%
CrowdStrike report of the incident: https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/
kid 4mo ago • 100%
Well, depends. If the user go to a captive portal to "authenticate" before the VPN could closes, than no. But, if the VPN can "pierce" through it (without any intervention from the AP), than yes. Anyways, If the user is willing to provide authentication data (like social media accounts, etc), nothing matters.
kid 4mo ago • 100%
kid 5mo ago • 100%
Interesting. I didn't know that syncthing does hole punching.
From a defense perspective, how would this work with an enterprise firewall, with UDP/TCP only allowed to specific destinations or specific sources. Example: only the internal DNS relay server can access 53/UDP and only the internal proxy server can access 80/443. What I mean is in a network with a very closed firewall, how would Syncthing be able to connect with peers?
kid 5mo ago • 100%
Instance Rules
Be respectful. Everyone should feel welcome here.
kid 5mo ago • 100%
Not necessarily. Torrent is a way to find a peer for direct connection or via a relay (of course that is more than that). Syncthing, even using a relay server, requires some ports available for at least outbound connection (22000 TCP/UDP or whatever port the relay is using). This should not be possible in a medium security network, let alone a defense network. I don't know if syncthing works without a direct connection (to the peer or relay, something like transport via http proxy).
kid 5mo ago • 100%
Honestly, I didn't think about vulnerability in SyncThing when I read the article. But I wondered why defense forces would have p2p open on their networks.
kid 5mo ago • 100%
By the messages that they are sending to customers, looks like is related to recent updates to the services, but nothing clear.